AqabaIX GlobePEER Route Server Guide
 Updated
by DE-CIX PS Team
Updated
by DE-CIX PS Team
The {{IXP}} route service (see RFC 7947 for a detailed description) facilitates the exchange of BGP announcements between peers at {{IXP}}. The route service consists of a pair of route servers for redundancy purposes. Each peer just needs to set up a BGP session per IP address family to the route servers in order to receive BGP announcements from other participating peers.
The software utilized to provide the service is BIRD. Of the two route servers, technically only one is required. However, in order to make full use of the route service, every peer is strongly encouraged to connect to both machines for redundancy purposes, so that if one machine is out of service (e.g. planned maintenance), the route service remains available.
BGP Session Parameters
This following table provides a brief overview of the BGP session parameters to connect to the route servers:
{{RS1_FQDN_UPPER}} |
|
{{RS2_FQDN_UPPER}} |
|
ASN |
|
AS-SET | IPv4: IPv6: |
Receive limit route server (our side) | IPv4: {{RECEIVE_LIMIT_RS_IPV4}} IPv6: {{RECEIVE_LIMIT_RS_IPV6}} |
Recommended route limit (your side) | IPv4: {{RECEIVE_LIMIT_CUSTOMER_IPV4}} IPv6: {{RECEIVE_LIMIT_CUSTOMER_IPV6}} |
BGP Announcement Filtering (Your Side)
You can safely accept any BGP announcements received via all route servers as {{IXP}} filters all incoming BGP announcements from all peers. The filtering mechanism is described in the section "{{IXP}} Side".
If you additionally want to filter on your side based on AS-SETs, you can do so by using one or more of the following AS-SETs:
AS-SET | Purpose |
| AS-SETs of all {{IXP}} customers (IPv4) |
| AS-SETs of all {{IXP}} customers (IPv6) |
| ASNs of all {{IXP}} customers |
BGP Announcement Filtering ({{IXP_SHORT}} Side)
The route servers filter all routes based on RPKI and IRRDB data as well as various other route hygiene criteria. RPKI and IRRDB filtering is based on the AS-SET the peer has provided. The AS-SET can be changed by contacting Customer Service, via IX-API or or self service portal.
Configurations are updated every 6 hours with a reconfiguration delay of two hours between rs1 and rs2. Don't forget to register your IP prefixes in the Internet Routing Registry (IRR) database well in advance (at least 24h before announcing the first time).
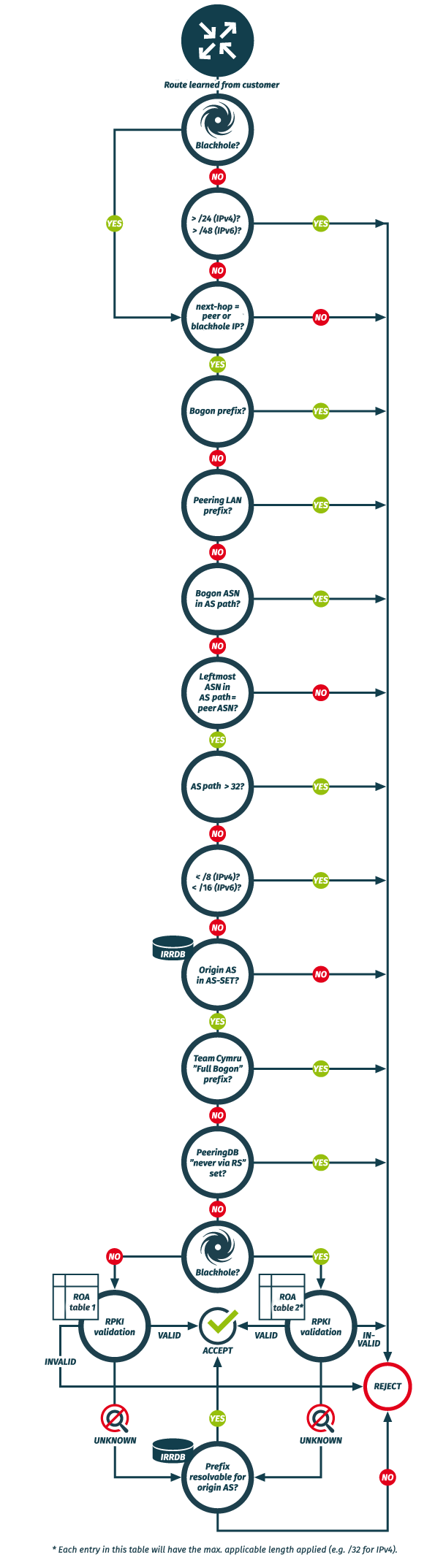
Bogon and Martian filtering
Please make sure not to announce routes that:
- are > /24 (IPv4) and > /48 (IPv6) (RFC 7454)
- have a different BGP next-hop than the IP of your own router
- are bogons/martians (private and reserved IP prefixes as defined by RFC 1918, RFC 2544, RFC 3927, RFC 5735, RFC 6598 and RFC 6890)
- are a {{IXP_SHORT}} peering LAN or a peering LAN of any of {{IXP_SHORT}}'s operated IXPs (please also do not announce any of our peering LANs in the DFZ!)
- contain bogon ASNs in the BGP AS path (private and reserved ASN numbers as defined by RFC 5398, RFC 6793, RFC 6696, RFC 7300 and RFC 7607
- differ in the leftmost ASN in the AS path from your own ASN
- have an AS path length > 32
- are < /8 (IPv4) and < /16 (IPv6)
- are listed in the Team Cymru Fullbogon list
- are marked as “never via route servers” in PeeringDB
IRR and RPKI validation
Any routes you announce will also be RPKI (RFC 6811, RFC 7115) validated and checked against Internet Routing Registry data. The AS-SET you provide to us will be recursively resolved. Then filtering is executed as follows:
- Origin ASN needs to be in customer AS cone. Make sure that your AS-SET is well maintained and that all your downstreams are included.
- Is the route a blackhole (RFC 7999)?
- If no, the route undergoes strict RPKI validation filtering (both
originand maximum prefix length (maxLength)):- if the result is
RPKI Valid, the route is accepted (a missing route object will have no implication in this case) - if the result is
RPKI Invalid, the route is rejected - if the result is
RPKI NotFound, we check if the route is resolvable for its origin ASN (this will be the case if a proper route object exists) and it might get accepted or rejected depending on the result**
- if the result is
- If yes, the route undergoes loose RPKI validation filtering (
originonly):- if the result is
RPKI Valid, the route is accepted - if the result is
RPKI Invalid, the route is rejected - if the result is
RPKI NotFound, we check if the route is resolvable for its origin ASN (this will be the case if a proper route object exists) and it might get accepted or rejected depending on the result**
- if the result is
- If no, the route undergoes strict RPKI validation filtering (both
**Loose filtering on IRRDB route objects
We perform loose filtering on IRRDB route objects. For example: If you have a route object for 46.31.120.0/21 we will also accept e.g. 46.31.120.0/22 and other more specifics (up to /24 and up to /32 for blackholes). If this is not a desired behavior, we strongly encourage you to create a ROA and set the maxLength attribute accordingly. As RPKI validation is performed before the IRRDB route object check, it will render all undesired more specifics as RPKI Invalid, which will result in rejection of these. Please note that this method only works for non-blackholes as we perform loose RPKI validation on blackholes (i.e. ignore maxLength).
Best Path Selection Process
Import
The route servers select the best path (best route) according to the following rules:
- prefer route with the highest
Local Preferenceattribute (can be set to 0 viaGRACEFUL_SHUTDOWNcommunity, default is100) - prefer route with the shortest AS path
- route origin: IGP (
i) > EGP (e) > incomplete (?) - prefer the lowest value of the
MED(Multiple Exit Discriminator)
MED is only compared between the same peer ASN (e.g. if you're announcing the same route(s) from ≥ 2 routers) - prefer the oldest known route (implies higher stability)
Each route is evaluated against the rules from top to bottom until a tie breaker is found.
Export
If an export filter is preventing the export of a previously selected best path route (e.g. due to traffic engineering via Action BGP Communities) the second best route (if available) is exported. If the second best route is also rejected on export, the third best route will be exported and so on.
Route Server Control
The route server can be controlled with BGP Communities. For more information, see {{IXP_SHORT}} {{IXP_PPN}} Route Server Action BGP Communities.
Route Server Route Tagging
We add BGP Communities to all routes to tag additional information like the route ingress, i.e. where it was injected into the {{IXP}} switching platform. For more details, see {{IXP_SHORT}} {{IXP_PPN}} Route Server Informational BGP Communities.
Session Types
From an operational point of view, it is advised to set up BGP sessions to both route servers, even if you do not want to peer with (i.e. advertise routes to) the route servers. This helps {{IXP}} staff to quickly monitor the availability of each peer. We offer two session types:
Session Type | Redistribution? | Routes received? | Looking Glass visibility? |
Public | ✅ | ✅ | ✅ |
Collector | ❌ | ❌ | ✅ |
Public Session (default)
We redistribute all your announcements to other peers while honoring the BGP communities which allow you to restrict your announcements and we advertise all announcements from other peers to you while honoring the BGP communities which allow others peers to restrict their announcements.
Collector Session (on demand)
You do not have to advertise any routes and you will not receive any routes from us on this session. Your session will only be visible in the Looking Glass.
If your decision not to establish BGP sessions with the route servers was made due to your peering policy, please contact us for establishing a collector session.
Example Configurations
The following section contains configurations examples for different router operating systems:
Cisco IOS
!
! Config example for Cisco IOS
! Peer and session templates, (S)AFI format and some basic filtering
! {{IXP}} route servers rs1, rs2
! Your example ASN: 64500 (replace with your real ASN)
! Local preference route servers: 125
!
router bgp 64500
bgp router-id <YOUR_ROUTER_ID>
! Requires all your sessions to reset to take effect (if not already enabled)
bgp graceful-restart
bgp graceful-restart restart-time 120
bgp graceful-restart stalepath-time 360
template peer-policy PP_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_COMMON
! Optional: Keep a pre-ingress-route-map copy of the peer table (if you have the memory; useful for debugging)
soft-reconfiguration inbound
! Strip private ASNs from BGP AS path
remove-private-as
! Allow sending of BGP standard communities to control your prefix advertisements
! For all available communities, please see "Action BGP Communities"
send-community
exit-peer-policy
!
template peer-policy PP_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_4
! Apply ingress route map
route-map RM_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN in
! Apply egress IPv4 route map
route-map RM_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4 out
! Please set maximum-prefix limit IPv4 mentioned in the RS Guide/PeeringDB
! maximum-prefix <recommended prefix limit (your side) IPv4>
inherit peer-policy PP_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_COMMON 1
exit-peer-policy
!
template peer-policy PP_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_6
! Apply ingress route map
route-map RM_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN in
! Apply egress IPv6 route map
route-map RM_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6 out
! Please set maximum-prefix limit IPv6 mentioned in the RS Guide/PeeringDB
! maximum-prefix <recommended prefix limit (your side) IPv6>
inherit peer-policy PP_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_COMMON 1
exit-peer-policy
!
template peer-session PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS
! ASN of {{IXP}} route servers
remote-as {{RS_ASN}}
! The route servers are passive and waiting for you side to initiate the sessions
transport connection-mode active
! Use BGP version 4 and skip version negotiation
version 4
! Please do not use aggressive timers (60/180 should be fine) to reduce the risk of flapping sessions
timers 60 180
exit-peer-session
!
! Our route servers are transparent: Ignore first AS in AS path not being your peer AS (i.e. {{RS_ASN}})
no bgp enforce-first-as
bgp log-neighbor-changes
neighbor {{RS1_IPV4}} inherit peer-session PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS
neighbor {{RS1_IPV4}} description {{RS1_FQDN_UPPER}}
neighbor {{RS1_IPV6}} inherit peer-session PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS
neighbor {{RS1_IPV6}} description {{RS1_FQDN_UPPER}}
neighbor {{RS2_IPV4}} inherit peer-session PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS
neighbor {{RS2_IPV4}} description {{RS2_FQDN_UPPER}}
neighbor {{RS2_IPV6}} inherit peer-session PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS
neighbor {{RS2_IPV6}} description {{RS2_FQDN_UPPER}}
!
address-family ipv4 unicast
! Some example IPv4 prefixes to announce
network 192.0.2.0
network 198.51.100.0
network 203.0.113.0
! We do not support IPv6 over IPv4 transport
no neighbor {{RS1_IPV6}} activate
no neighbor {{RS2_IPV6}} activate
neighbor {{RS1_IPV4}} activate
neighbor {{RS1_IPV4}} inherit peer-policy PP_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_4
neighbor {{RS2_IPV4}} activate
neighbor {{RS2_IPV4}} inherit peer-policy PP_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_4
exit-address-family
!
address-family ipv6 unicast
! Some example IPv6 prefixes to announce
network 2001:DB8:1234::/48
network 2001:DB8:ABCD::/48
network 2001:DB8:FFFF::/48
neighbor {{RS1_IPV6}} activate
neighbor {{RS1_IPV6}} inherit peer-policy PP_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_6
neighbor {{RS2_IPV6}} activate
neighbor {{RS2_IPV6}} inherit peer-policy PP_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_6
exit-address-family
!
! Use new BGP community format
ip bgp-community new-format
!
! We will not advertise IPv4 prefixes less specific than /8 and more specific than /24
! Exception: Blackhole next-hop and/or BLACKHOLE Community is set.
! Please allow up to /32 if you wish to receive all blackholed prefixes from the route servers
! Prefix list example: Allow every IPv4 prefix up to /32 from the route servers
ip prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN_4 seq 5 permit 0.0.0.0/0 le 32
!
! We will not advertise IPv6 prefixes less specific than /16 and more specific than /48
! Exception: Blackhole next-hop and/or BLACKHOLE Community is set.
! Please allow up to /128 if you wish to receive all blackholed prefixes from the route servers
! Prefix list example: Allow every IPv6 prefix up to /128 from the route servers
ipv6 prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN_6 seq 5 permit ::/0 le 128
!
! We do not accept IPv4 prefixes less specific than /8 and more specific than /24
! Exception: Up to /32 allowed when Blackhole next-hop and/or BLACKHOLE Community is set
! Prefix list example: Make sure to only advertise your own IPv4 prefixes/those of your customers
ip prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4 seq 5 permit 192.0.2.0/24
ip prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4 seq 10 permit 203.0.113.0/24
!
! We do not accept IPv6 prefixes less specific than /16 and more specific than /48
! Exception: Up to /128 allowed when Blackhole next-hop and/or BLACKHOLE Community is set
! Prefix list example: Make sure to only advertise your own IPv6 prefixes/those of your customers
ipv6 prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6 seq 5 permit 2001:DB8:1234::/48
ipv6 prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6 seq 10 permit 2001:DB8:FFFF::/48
!
! Prefix list example: IPv4 prefixes to blackhole
ip prefix-list PL_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_4 seq 5 permit 198.51.100.0/24
!
! Prefix list example: IPv6 prefixes to blackhole
ipv6 prefix-list PL_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_6 seq 5 permit 2001:DB8:ABCD::/48
!
! Route-Map example: Set local-preference for route servers to 125
route-map RM_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN permit 10
match ip address prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN_4
match ipv6 address prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN_6
set local-preference 125
!
! Route-Map example:
! Use community 0:64501 for not allowing AS64501 to receive your prefixes
! Use community {{RS_ASN_SUB}}:{{RS_ASN_SUB}} for allowing the route servers to advertise your prefixes to all (other) peers
! For all available communities, please see "Action BGP Communities"
route-map RM_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4 permit 10
match ip address prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4
set community {{RS_ASN_SUB}}:{{RS_ASN_SUB}} 0:64501 additive
!
! Route-Map example: Blackhole IPv4 prefixes
route-map RM_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4 permit 20
match ip address prefix-list PL_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_4
set community {{RS_ASN_SUB}}:{{RS_ASN_SUB}} additive
set community 65535:666 additive
!
! Route-Map example:
! Use community 0:{{RS_ASN_SUB}} in combination with {{RS_ASN_SUB}}:64502 to allow no one except AS64502 to receive your IPv6 prefixes
route-map RM_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6 permit 10
match ipv6 address prefix-list PL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6
set community 0:{{RS_ASN_SUB}} additive
set community {{RS_ASN_SUB}}:64502 additive
!
! Route-Map example: Blackhole IPv6 prefixes
route-map RM_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6 permit 20
match ipv6 address prefix-list PL_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_6
set community {{RS_ASN_SUB}}:{{RS_ASN_SUB}} additive
set community 65535:666 additive
!
Cisco IOS XR
!!
!! Config example for Cisco IOS XR
!! Session-, AF- and neighbor groups as well as some basic filtering
!! {{IXP}} route servers rs1, rs2
!! Your example ASN: 64500 (replace with your real ASN)
!! Local preference route servers: 125
!!
!
!! We do not accept IPv4 prefixes less specific than /8 and more specific than /24
!! Exception: Up to /32 allowed when Blackhole next-hop and/or BLACKHOLE Community is set
!! Prefix set example: Make sure to only advertise your own IPv4 prefixes/those of your customers
prefix-set PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4
192.0.2.0/24,
203.0.113.0/24
end-set
!
!! We do not accept IPv6 prefixes less specific than /16 and more specific than /48
!! Exception: Up to /128 allowed when Blackhole next-hop and/or BLACKHOLE Community is set
!! Prefix set example: Make sure to only advertise your own IPv6 prefixes/those of your customers
prefix-set PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6
2001:db8:1234::/48,
2001:db8:ffff::/48
end-set
!
!! Prefix set example: IPv4 prefixes to blackhole
prefix-set PS_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_4
198.51.100.0/24
end-set
!
!! Prefix set example: IPv6 prefixes to blackhole
prefix-set PS_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_6
2001:db8:abcd::/48
end-set
!
!! Use this community for allowing the route servers to advertise your prefixes to all peers
!! For all available communities, please see "Action BGP Communities"
!! Community set example: Community set for {{IXP}} "advertise to all peers" community
community-set CS_{{IXP_SHORT_UPPER}}_ADVERTISE_TO_ALL_PEERS
{{RS_ASN_SUB}}:{{RS_ASN_SUB}}
end-set
!
community-set CS_{{IXP_SHORT_UPPER}}_BLACKHOLE
65535:666
end-set
!
!! We will not advertise IPv4 prefixes less specific than /8 and more specific than /24
!! Exception: Blackhole next-hop and/or BLACKHOLE Community is set
!! Please allow up to /32 if you wish to receive all blackholed prefixes from the route servers
!! Route Policy example: Allow every IPv4 prefix from the route servers and set local preference to 125
route-policy RPL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN_4
set local-preference 125
pass
end-policy
!
!! We will not advertise IPv6 prefixes less specific than /16 and more specific than /48
!! Exception: Blackhole next-hop and/or BLACKHOLE Community is set
!! Please allow up to /128 if you wish to receive all blackholed prefixes from the route servers
!! Route Policy example: Allow every IPv6 prefix from the route servers and set local preference to 125
route-policy RPL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN_6
set local-preference 125
pass
end-policy
!
!! Route Policy example:
!! Advertise IPv4 prefixes from prefix sets PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4 and PS_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_4 (prefixes to blackhole)
!! Use community 0:64501 for not allowing AS64501 to receive your prefixes
!! Use community {{RS_ASN_SUB}}:{{RS_ASN_SUB}} for allowing the route servers to advertise your prefixes to all (other) peers
!! Set {{IXP}} BLACKHOLE Community
!! For all available communities, please see "Action BGP Communities"
route-policy RPL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4
if destination in PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4 then
set community CS_{{IXP_SHORT_UPPER}}_ADVERTISE_TO_ALL_PEERS additive
set community (0:64501) additive
pass
!! Blackhole IPv4 prefixes
elseif destination in PS_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_4 then
!! Allow all peers to receive your blackholed prefixes
set community CS_{{IXP_SHORT_UPPER}}_ADVERTISE_TO_ALL_PEERS additive
!! Set BLACKHOLE Community
set community CS_{{IXP_SHORT_UPPER}}_BLACKHOLE additive
pass
else
drop
endif
end-policy
!
!! Route Policy example:
!! Advertise IPv6 prefixes from prefix sets PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6 and PS_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_6 (prefixes to blackhole)
!! Use community 0:{{RS_ASN_SUB}} in combination with {{RS_ASN_SUB}}:64502 to allow no one except AS64502 to receive your IPv6 prefixes
!! Set {{IXP}} BLACKHOLE Community
route-policy RPL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6
if destination in PS_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6 then
set community (0:{{RS_ASN_SUB}}) additive
set community ({{RS_ASN_SUB}}:64502) additive
pass
!! Blackhole IPv6 prefixes
elseif destination in PS_{{IXP_SHORT_UPPER}}_BLACKHOLE_OUT_6 then
!! Allow all peers to receive your blackholed prefixes
set community CS_{{IXP_SHORT_UPPER}}_ADVERTISE_TO_ALL_PEERS additive
!! Set BLACKHOLE Community
set community CS_{{IXP_SHORT_UPPER}}_BLACKHOLE additive
pass
else
drop
endif
end-policy
!
router bgp 64500
bgp router-id <YOUR_ROUTER_ID>
bgp graceful-restart
address-family ipv4 unicast
!! Some example IPv4 prefixes to announce
network 192.0.2.0/24
network 198.51.100.0/24
network 203.0.113.0/24
!
address-family ipv6 unicast
!! Some example IPv6 prefixes to announce
network 2001:db8:1234::/48
network 2001:db8:abcd::/48
network 2001:db8:ffff::/48
!
af-group AG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_4 address-family ipv4 unicast
!! Allow sending of BGP standard communities to control your prefix advertisements
!! For all available communities, please see "Action BGP Communities"
send-community-ebgp
!! Inbound IPv4 policy
route-policy RPL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN_4 in
!! Outbound IPv4 policy
route-policy RPL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_4 out
!! Please set maximum-prefix limit IPv4 mentioned in the RS Guide/PeeringDB
!! maximum-prefix <recommended prefix limit (your side) IPv4> 75
!! Strip private ASNs from BGP AS path
remove-private-AS
!! Optional: Keep a pre-ingress-route-map copy of the peer table even if route refresh is supported (if you have the memory; useful for debugging)
soft-reconfiguration inbound always
!
af-group AG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_6 address-family ipv6 unicast
!! Allow sending of BGP standard communities to control your prefix advertisements
!! For all available communities, please see "Action BGP Communities"
send-community-ebgp
!! Inbound IPv6 policy
route-policy RPL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_IN_6 in
!! Outbound IPv6 policy
route-policy RPL_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_OUT_6 out
!! Please set maximum-prefix limit IPv6 mentioned in the RS Guide/PeeringDB
!! maximum-prefix <recommended prefix limit (your side) IPv6> 75
!! Strip private ASNs from BGP AS path
remove-private-AS
!! Optional: Keep a pre-ingress-route-map copy of the peer table even if route refresh is supported (if you have the memory; useful for debugging)
soft-reconfiguration inbound always
!
session-group SG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS
!! ASN of {{IXP}} route servers
remote-as {{RS_ASN}}
!! Please do not use aggressive timers (60/180 should be fine) to reduce the risk of flapping sessions
timers 60 180
!! Our route servers are transparent: Ignore first AS in AS path not being your peer AS (i.e. {{RS_ASN}})
enforce-first-as disable
!! Allow BGP graceful restart
graceful-restart
!! The route servers are passive and waiting for you side to initiate the sessions
session-open-mode active-only
!
neighbor-group NG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_4
use session-group SG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS
address-family ipv4 unicast
use af-group AG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_4
!
!
neighbor-group NG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_6
use session-group SG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS
address-family ipv6 unicast
use af-group AG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_6
!
!
neighbor {{RS1_IPV4}}
use neighbor-group NG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_4
description {{RS1_FQDN_UPPER}}
!
neighbor {{RS1_IPV6}}
use neighbor-group NG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_6
description {{RS1_FQDN_UPPER}}
!
neighbor {{RS2_IPV4}}
use neighbor-group NG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_4
description {{RS2_FQDN_UPPER}}
!
neighbor {{RS2_IPV6}}
use neighbor-group NG_{{IXP_SHORT_UPPER}}_ROUTE_SERVERS_6
description {{RS2_FQDN_UPPER}}
!
!
end